A user could access Ensighten Real-Time Tag Management System by adding the URL parameter "ensightenVT=1" on the pinpoint.microsoft.com. This would allow to check a couple of Ensighten options.
Proof of concept #1:
http://pinpoint.microsoft.com/en-US/applications/search?sort=rating&q=nothing&fcrc=PRT&ensightenVT=1
After this point, a reflected DOM XSS it's present on a couple of places and adding the vector on the previous URL:
Proof of concept #2:
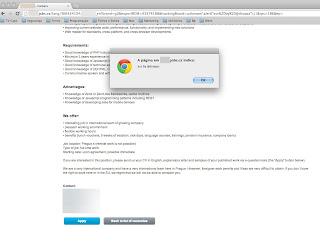
#"><img src=x onerror=prompt(1);>
... and navigating on some Ensighten options, the vector would execute successfully and automatically.
This was due to a lack of sanitizing location.hash.
Microsoft Security Response Center replied:
Thank you for reporting this to us. I want to let you know that we have been able to finish our review of this issue and have fixed this in an online services update. I would like to provide you with an acknowledgement for working with us on our Online Researcher Acknowledgement page at http://technet.microsoft.com/en-us/security/cc308589.After getting my name on Google and eBay, currently I'm also listed on Microsoft: (http://technet.microsoft.com/en-us/security/cc308589).
Timeline:
19 Mar 2013: Reported to Microsoft
19 Mar 2013: Microsoft reported that will take a look into it
22 Mar 2013: Microsoft reported that this issue is fixed in an online services update
13 Jun 2013: Full disclosure